A friend tried to make his first malware analysis and had some issue with the sample: f63f9d683d7e756aee3b353d2836a6d2 (called IM51332.JPG-www.myspace.com.exe). I decided to help him.
- MD5: f63f9d683d7e756aee3b353d2836a6d2
- SHA1: 14550cd11d0a08b5d1682f6bb588a3450b81074b
- Driver detection: https://www.virustotal.com/file/24acdbbaeb51a606bcee18ccc5b5e4091aa29aa5501c6a5c5fd43a8cdbd88ae2/analysis/
- VT Detection ratio: 34 / 41 (05/08/2012)
Analysis
The sample seems to be packed. But I decided to not unpack it and launch it on VirtualBox.
I performed a dump of the memory and analyse it with volatility:
rootbsd@malware.lu:~$ vol.py -f mal.dmp pslist
Volatile Systems Volatility Framework 2.1_alpha
Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit
---------- -------------------- ------ ------ ------ -------- ------ ------ -------------------- --------------------
0x812ed020 System 4 0 55 301 ------ 0
0xffbaeb10 smss.exe 368 4 3 19 ------ 0 2012-05-21 15:20:54
0x811248e0 csrss.exe 584 368 11 479 0 0 2012-05-21 15:20:54
0x81197248 winlogon.exe 608 368 22 514 0 0 2012-05-21 15:20:54
0x811275a8 services.exe 652 608 16 258 0 0 2012-05-21 15:20:54
0x8112d7e0 lsass.exe 664 608 25 379 0 0 2012-05-21 15:20:54
0xffbd7a78 VBoxService.exe 820 652 8 106 0 0 2012-05-21 15:20:54
0x81180c30 svchost.exe 864 652 19 200 0 0 2012-05-21 06:20:56
0x811a6b28 svchost.exe 952 652 10 257 0 0 2012-05-21 06:20:56
0xffac4218 svchost.exe 1044 652 86 1532 0 0 2012-05-21 06:20:56
0xffabbd08 svchost.exe 1092 652 8 87 0 0 2012-05-21 06:20:56
0x8116cda0 svchost.exe 1132 652 13 172 0 0 2012-05-21 06:20:56
0x8112eca8 spoolsv.exe 1544 652 14 111 0 0 2012-05-21 06:20:57
0xffa93b00 explorer.exe 1556 1504 20 517 0 0 2012-05-21 06:20:57
0x8112fda0 VBoxTray.exe 1700 1556 6 64 0 0 2012-05-21 06:20:57
0xffb95da0 svchost.exe 1904 652 6 108 0 0 2012-05-21 06:21:05
0xffa01a98 alg.exe 1076 652 7 108 0 0 2012-05-21 06:21:09
0x81178278 wscntfy.exe 1188 1044 1 31 0 0 2012-05-21 06:21:11
0x81188da0 wuauclt.exe 1956 1044 8 180 0 0 2012-05-21 06:21:51
0x811323c0 wuauclt.exe 248 1044 5 136 0 0 2012-05-21 06:22:05
0xff9e7da0 infocard.exe 1500 1012 7 144 0 0 2012-08-27 11:05:50
0x81244c60 netsh.exe 1228 1500 0 -------- 0 0 2012-08-27 11:05:50 2012-08-27 11:05:55
0x8116e650 IEXPLORE.EXE 1492 864 27 635 0 0 2012-08-27 11:05:51
0xff9bd6e8 wmiprvse.exe 452 864 11 226 0 0 2012-08-27 11:05:52
0xff9aa588 ctfmon.exe 2072 1492 1 82 0 0 2012-08-27 11:05:54
0xff99c9a0 IEXPLORE.EXE 2120 1492 29 688 0 0 2012-08-27 11:05:55
The process 1500 (infocard.exe) and his chlid (netsh.exe) were strange.
I made a dump of the process 1500:
rootbsd@malware.lu:~$ vol.py -f mal.dmp procmemdump -D /tmp/ -p 1500
Volatile Systems Volatility Framework 2.1_alpha
************************************************************************
Dumping infocard.exe, pid: 1500 output: executable.1500.exe
rootbsd@malware.lu:~$ file /tmp/executable.1500.exe
/tmp/executable.1500.exe: PE32 executable (GUI) Intel 80386, for MS Windows
The PID 1500 was a file dropped by the sample.
I opened it with IDA Pro and discovered some encoded strings. Each encoded string was follow by: call sub_406C78.
Here the function:
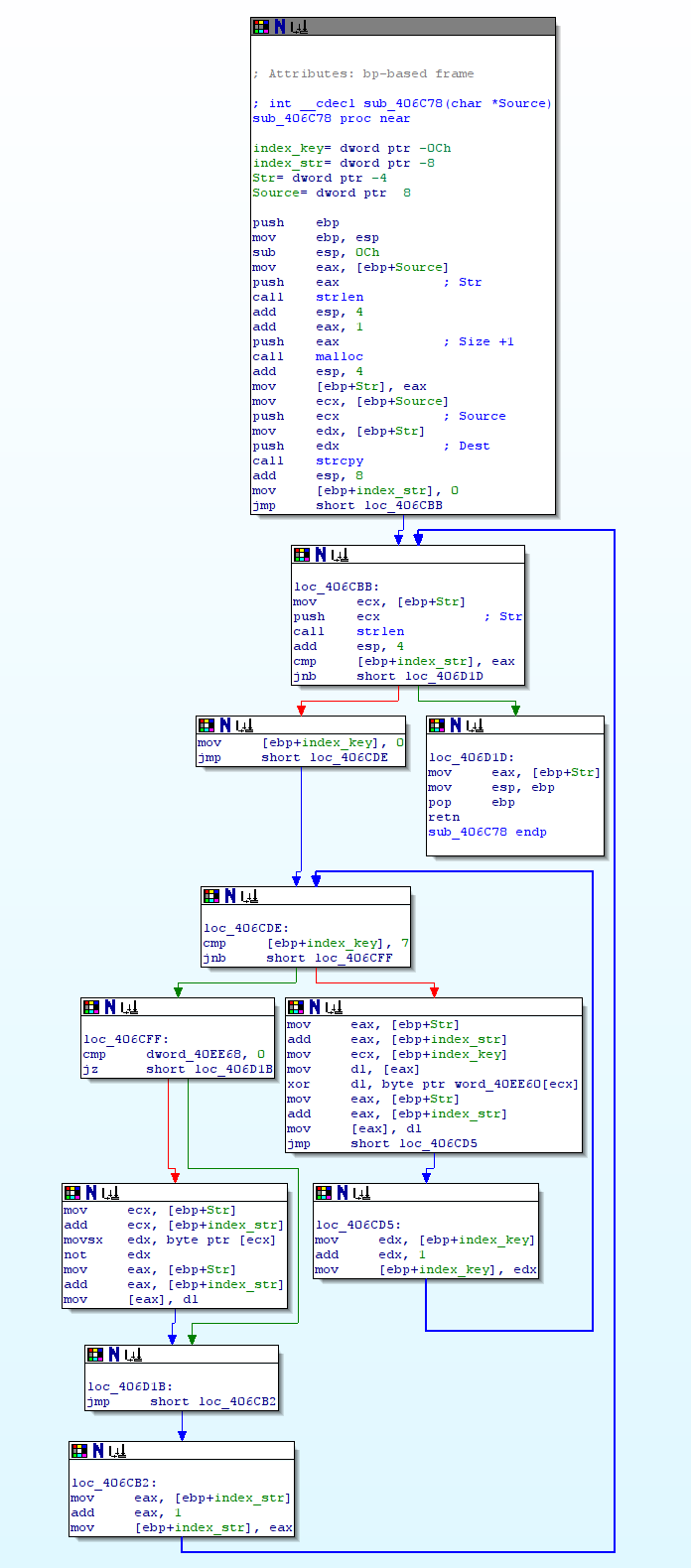
The argument of the function is then encoded string. The encoded string is copied in ebp+Str.
Each character of the strings is xored by word_40EE60 : x0rb0t.
The schema on the encoding is:
- str[1] xor(x) = char[1]
- char[1] xor(0) = char[2]
- char[2] xor(r) = char[3]
- char[3] xor(b) = char[4]
- char[4] xor(0) = char[5]
- char[5] xor(t) = char[6]
At the end a NOT is applied to the char[6].
Here a ruby script to decode the strings:
#!/usr/bin/env ruby1.9.1
malwareFile = File.open(ARGV[0], 'r')
malwareFile.seek(0xee60, IO::SEEK_SET)
key = malwareFile.sysread(0x7)
file = File.open(ARGV[0], 'r')
file.seek(0xd12c, IO::SEEK_SET)
str = file.sysread(8)
i=0
str.each_byte { |x|
while i != 7 do
x = x ^ key[i].ord
i=i+1
end
putc ~x
i=0
}
rootbsd@malware.lu:~$ ./x0rb0t.rb /tmp/executable.1500.exe
%windir%
The encoding allows to be testing in the full binary:
#!/usr/bin/env ruby1.9.1
malwareFile = File.open(ARGV[0], 'r')
malwareFile.seek(0xee60, IO::SEEK_SET)
key = malwareFile.sysread(0x7)
file = File.open(ARGV[0], 'r')
file.seek(0x0, IO::SEEK_SET)
str = file.sysread(File.stat(ARGV[0]).size)
i=0
str.each_byte { |x|
while i != 7 do
x = x ^ key[i].ord
i=i+1
end
putc ~x
i=0
}
rootbsd@malware.lu:~$ ./x0rb0t.rb /tmp/executable.1500.exe | string
*!*@*
infocard.exe
Firewall Administrating
%windir%
#info
Crack.exe
usb_driver.com
dbsarticles.com
#imb
test
http://get.articleslinked.com/univ.php
S3`v_,E
Z_,E
XH"
S3`v_,E
Z_,E
XH"
S3`v_,E
Z_,E
XH"
S3`v_,E
Z_,E
\88@
C1v~
C1v~
C1v~
C1v~
C1v~
C1v~
C1v~
}L$R
1aS&
JOIN
PART
MODE
PRIVMSG
NOTICE
PONG
NICK
PASS
USER
QUIT
PING
U|n1
All strings are decoded.
MISC
After a quick analyses:
- the sample is persistant and add its startup in the registry : SOFTWARE\Microsoft\Windows\CurrentVersion\Run\
- the sample connect to the HTTP server: get.articleslinked.com (65.19.157.237) with a specific User-Agent: 8277016453
- the sample seems to have an IRC module and connect to dbsarticles.com:2345 (69.43.160.200) but the server is down…